Solved : Argo-workflow dex integration without argocd dex
youtube video : https://youtu.be/4HTFGlAEqJg
Most of you guys who is reading the article must be wondering how I can enable argo workflow SSO without using ArgoCd dex. So many drawbacks.
If I don’t want to understand argocd structure I will have to install whole ArgoCD with argocd-dex in order to get my Argo workflow sso working and believe me I went through the pain and its not fun.
Argo workflow itself does not have any document which says how multiple provider integrate with ArgoCD Dex.
Doumentation is not clear enought about the integration and which provider directly works with Argo workflow and for which one you need to use dex.
and the list goes on…
Argo workflow does work directly with some of the providers which I tested:
KeyClock
Okta
It does not work with following (tested and proven)
GitHub
Azure OIDC
and there may be some more.
So, what is the solution if Argo workflow does not provide support for all OIDC provide.
Its DEX
Now how I integrate with Dex. So according to Argo workflow if we are not supporting any OIDC provider you should use argocd dex :). Amazing huh.. But why I will install ArgoCD if I don’t need it just to use ArgoCD Dex.
This is where I got to get Argoworkflow working with stand alone Dex instead of ArgoCD Dex.
Now you must be wondering why my keep on repeating argocd dex and dex separately. So to answer you guys its because Argo team has integarted dex in their argocd binary and now its called argocd dex :). I never tried it directly.
Now, If I am done complaining about all, lets get to the point and get our Argo Workflow working with Stand alone DEX.
I have a free GCP account and using a GKE cluster for the demo and has some external IP reserved in order to get it work in one go.
Prerequisites:
Get two static ip for your service. One for Dex, another one for Argo workflow server.
Create an OIDC Application for AzureAD using the following link: https://docs.microsoft.com/en-us/power-apps/maker/portals/configure/configure-openid-settings
If you would like to try argo workflow using GitHub OIDC create a Application using following link for GitHub :
https://access.redhat.com/documentation/en- us/red_hat_quay/3.2/html/use_red_hat_quay/github-app
- Make sure you are adding the following URL as a call back when setting up the application. You can always change this.
https://<DEX_LoadBalancer_IP>:5556/dex/callback
For Microsoft Connector(Azure OIDC):
* Download following repo:
```plaintext
git clone git@github.com:tiwarisanjay/argoworkflow-dex.git
cd argoworkflow-dex
- Run following script which will
Create Self signed certificate.
Create tls secret for dex to secure connection.
Create config-map with root ca for argo workflow
Script will ask for
Namespace : default is argo. Lets keep it that way.
clientID : You got this ID when you created OIDC application for GitHub or Microsoft.
Client Secret : You got this secret when you Created OIDC application using GitHub or Microsoft.
Load Balancer IP : Load balancer IP for DEX secret.(Yes I didn’t try ingress. I will try it and will update the doc. )
./pre-req.sh
Script will create secret
argo-workflows-ssoandtls-secretalong with a config-mapdex-cain argo namespace.Now lets add the helm repo :
helm repo add helm-chart-repo https://tiwarisanjay.github.io/helm-chart-repo
- Update helm repo
helm repo update
- Search helm repo if you have connector helm charts
helm search repo helm-chart-repo/OUTPUT WILL BE ::: NAME CHART VERSION APP VERSION DESCRIPTIONhelm-chart-repo/awdex-github 0.1.0 v2.30.0 A Helm chart for argo workflow integration with...helm-chart-repo/awdex-microsoft 0.3.0 v2.30.0 A Helm chart for argo workflow integration with...helm-chart-repo/test-app 0.1.0 1.16.0 A Helm chart for Kubernetes
## For Microsoft connector
- create a values file as following
dex:loadBalancerIP: 34.139.129.139config:clientid: abcdd84d-0101-1212-2323-df57fasdfftenantid: 09sdfks-2aqa-45d2-3433-54f52asdffdclientSecret: Rtu3c~6RUXdwcMNZ-Flskeif094r5kNFl~urXissuer: https://34.139.129.139:5556/dex # Dex URL ex : https://34.139.129.139:5556/dexstaticClient:redirectUrl: https://32.113.57.83:2746/oauth2/callback # Argo workflow redirect url ex : https://32.113.57.83:2746/oauth2/callbackargo-workflows:server:loadBalancerIP: 32.113.57.83sso:issuer: https://34.139.129.139:5556/dexclientId:name: argo-workflows-ssokey: client-idclientSecret:name: argo-workflows-ssokey: client-secretredirectUrl: https://32.113.57.83:2746/oauth2/callbackrbac:enabled: false
- Install microsoft helm connector
helm install upgrade helm-chart-repo/awdex-microsoft -f azure-values.yaml -n argo
- There should be three pod in argo namespace :
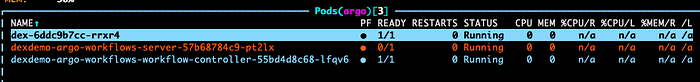
If argo-woflow-server pod does not come up and throws any error just restart it as it has dependency for dex pod.
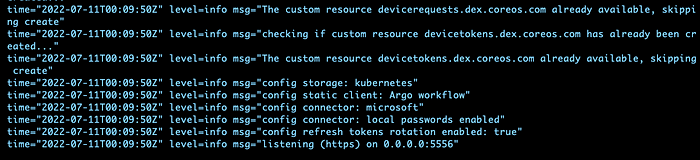
dex log tail
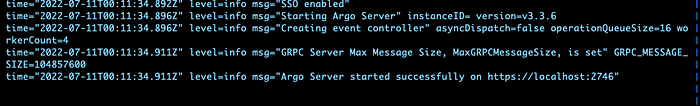
- argo workflow server log tail
Validate your services which should have load balancer.
if all pods are up go browser and paste your argo workflow URL. This is loadbalancer ip.:2746
- Accept the security risk as we are using self signed cert and it should show up following page
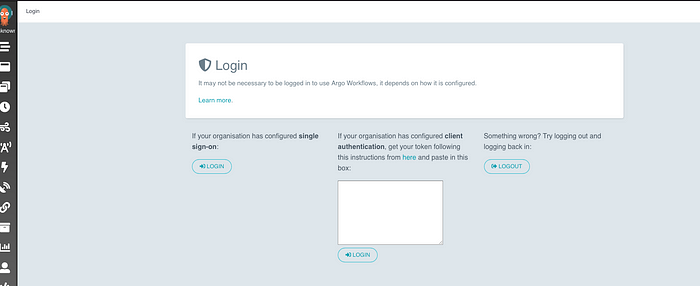
- Click on single-sign-on Login and you should see following page:
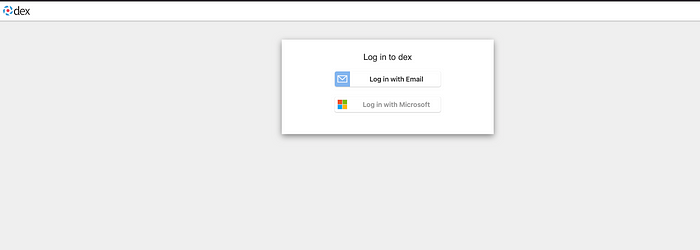
- Click on Log in with Microsoft. Authenticate with AzureAD and if your call back it correct it should take you back at following page:
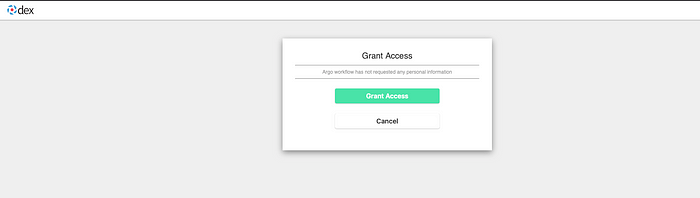
- Grant Access and it will take you to following screen
Wow……..
You are ready with your SSO integration using Microsoft Azure OIDC provider ………
Same can be done for GitHub too just following following ReadME for github.
https://github.com/tiwarisanjay/argoworkflow-dex/blob/develop/charts/awdex-github/README.md
If you get stuck somewhere you can following the AzureAD readme :
https://github.com/tiwarisanjay/argoworkflow-dex/blob/develop/charts/awdex-microsoft/README.md
Some Missing Points :
I didn't cover RBAC which can be enabled for GitHub using teams and can be used Groups in Microsoft.
I didn't cover localhost which is easy with GitHub but complicated using Microsoft because of some caveats in Dex and Microsoft. Ping me on Slack and I will answer about the same.
I am planning to get a Youtube video soon on topic and will update it when its ready. For more info you can read the code in the repo you cloned above :)
Thank you for reading and let me know in case of any question.